IoT cybersecurity
Secure your IoT devices and systems with TeamViewer Tensor


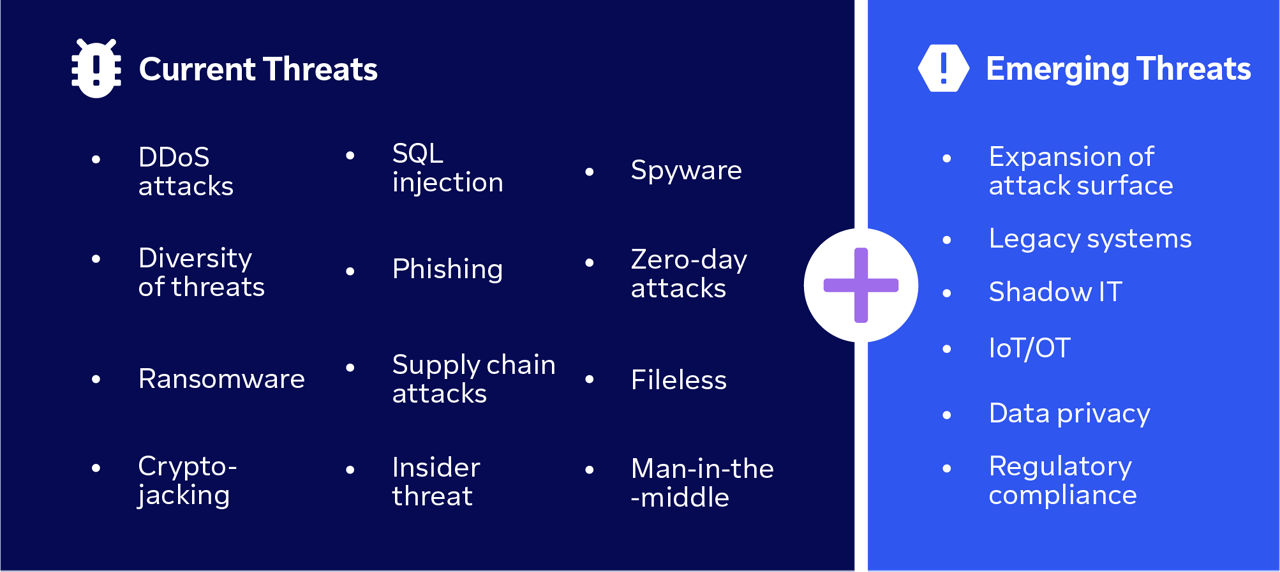
However, the sheer volume and diversity of 'things' that comprise IoT means there is an ever-growing number of devices within your organization that contain a considerable amount of sensitive data. As a result, there are more opportunities for cybercriminals and hackers to compromise your security and access this data.
So how are corporates addressing these significant IoT cybersecurity challenges to ensure they operate safely, securely, and reliably? Learn more about it with TeamViewer.
Given the extensive increase in IoT-connected devices lately — a trend which is forecast to continue — the risk of malware and ransomware attacks to exploit IoT vulnerabilities has increased. And cyberattacks on IoT devices can have serious consequences for your business.
IoT botnet malware is one of the most popular tools of cybercriminals. Hackers infect your IoT devices with malware and use them as a botnet — a network of interconnected, compromised devices that can be controlled remotely. These botnets can be used to infect more machines, initiate malicious activity, or create DDoS attacks.
During a distributed denial-of-service (DDoS) attack, hackers overload your website, network, or servers with malicious traffic or thousands of requests, preventing your IT infrastructure from functioning properly. This affects the availability and reliability of your devices and systems across the network, thereby potentially interrupting supply chains, delaying deliveries, or disrupting customer service.
Hackers steal sensitive or confidential data from your IoT devices or networks, such as customer information, financial records, trade secrets, or intellectual property. Such a breach not only leads to reputational damage and competitive disadvantage but also opens your company up to legal liability and the possibility of regulatory fines.
Hackers take control of your IoT devices remotely and manipulate their functions or settings, causing physical damage, disruption, or harm to your business operations, assets, or employees. For example, hackers could sabotage production lines, compromise quality control, or endanger worker safety.
From point-of-sale systems in retail to smart environmental controls in the office, IoT is an evolving technology that offers many benefits for every kind of business. However, IoT devices also face significant cybersecurity challenges that need to be addressed to ensure their safe and reliable operation.
Many companies turn to TeamViewer Tensor to secure their IoT devices centrally, remotely, and automatically. With TeamViewer Tensor, you can:
Thanks to the popularity and convenience of IoT for enterprise, there is now a large selection of devices from various manufacturers available on the market. These devices may have different security standards, configurations, and capabilities, making it difficult to manage and secure them in a consistent and coordinated manner.
Managing this heterogeneous IoT estate efficiently is an increasing headache for global businesses — particularly when faced with the additional complexity of complying with relevant security and privacy laws, regulations, and standards. TeamViewer lets you manage your devices centrally and securely.
The introduction of IoT devices increases the number of entry points and vectors for cyberattacks, as each connection can be exploited or compromised by hackers. What’s more, some IoT devices may interact with other networks, such as cloud services or communication systems, creating interdependencies and cascading effects that can amplify the impact of an attack.
TeamViewer Tensor helps you access, control, manage, and secure all your IoT devices from a single platform. With tools such as asset inventory, configuration and patch management, you can proactively manage your estate as well as identify and close IoT vulnerabilities. And you get full control of who has access to specific devices thanks to Tensor’s conditional access and user management features.
TeamViewer Tensor is one of the leading cloud-based enterprise connectivity platforms. By adopting TeamViewer Tensor, you enhance cybersecurity for your IoT ecosystem.
Tensor also integrates with many of the platforms commonly used within large organizations, such as
TeamViewer Tensor provides device-agnostic connectivity for all devices in the IoT ecosystem. To learn more about Tensor and how it can help you unlock the potential of the IoT, schedule a demo today.
Securing IoT devices against hackers and cyberattacks is essential for safeguarding infrastructure and networks, protecting privacy and personal information, and mitigating financial and reputational harm.