Provide secure remote access for your business
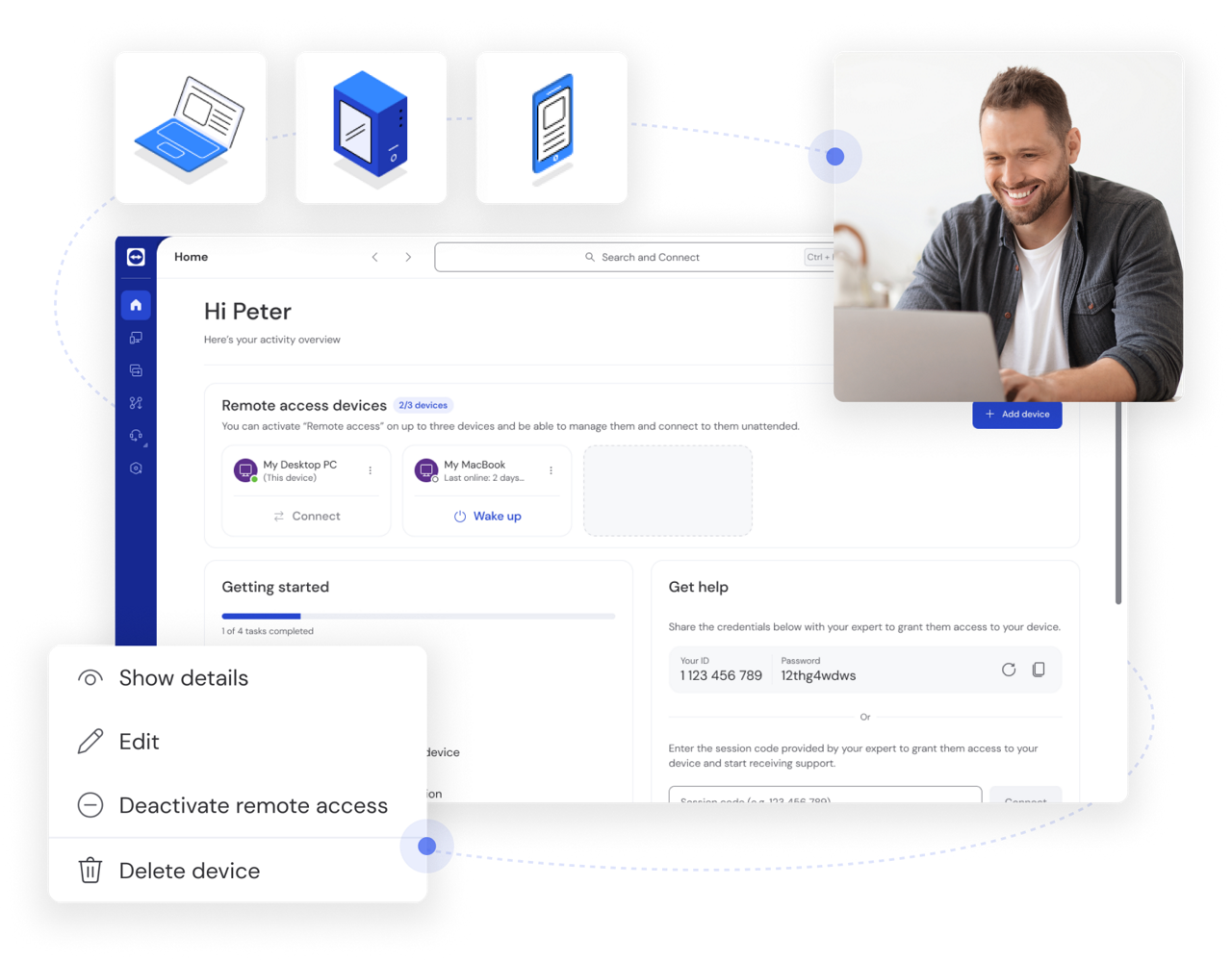

Secure remote access is one of the most critical aspects of corporate network security. As hybrid work models become the norm and the number of employees working from home grows, companies are looking for secure remote access solutions that combine ease of use with security and protection. After all, the priority must always be maintaining security when users are remotely accessing sensitive data and critical applications.
Data and information are valuable assets in the day-to-day operations of a company. Secure remote access is a critical step in protecting this sensitive data from unauthorized access by third parties.
Businesses have access to technologies that, when combined, make remote access more secure. The best technology for you will depend on your individual needs, but will likely include one or more of the following services:
Cloud access security brokers
Endpoint protection
Firewalls
Multifactor authentication
Zero trust network access
The use of secure remote access solutions is becoming increasingly important as cyber threats and attacks continue to evolve. As key elements in today’s IT environment, these technologies help protect business-critical data and keep assets safe. However, implementing secure remote access solutions alone is not enough — businesses need to supplement their investment in technology by training employees on data protection and third-party threats, introducing cybersecurity policies and implementing regular security hygiene measures to maximize security and minimize risks.
A well-planned strategy for deploying and maintaining secure remote access to a corporate network offers a wide range of benefits across your organization. These benefits extend beyond the IT department to manufacturing, sales and marketing, HR, logistics, and management.
Nowadays, remote access from a PC at home, laptop, smartphone, or tablet is taken for granted. However, this type of access creates new security challenges. Employee training raises awareness of the issues around secure remote access. Together with defined security policies, it is critical to minimize risk.
Endpoint protection provides another layer of IT security for businesses. With endpoint protection software, users can securely access their network on any device (endpoint), anytime from anywhere. By examining files, processes, and system activity, endpoint security software protects any endpoint (on-premises or off-site) from being breached or sessions being hijacked by malicious third parties.
The shift towards digital transformation and remote work means that a secure web gateway is a critical service for any business. Users rely heavily on web-based applications for collaboration, messaging, video conferencing, etc. This means that they are constantly accessing the web. By implementing secure remote control over internet access, organizations can protect against web-based malware threats, such as phishing or ransomware, and prevent access to unauthorized sites.
A well-designed secure remote access system allows users to connect to a network from any corporate or personal PC, laptop, smartphone, or tablet. Regardless of which device they are working on, users benefit from security that was previously only available at the workplace. At the same time, administrators enjoy simplified remote management and can implement services such as access authorization, session monitoring and management, and advanced analytics.
Antivirus software needs to be installed on each device. And to ensure that corporate resources are secure regardless of where employees access data and programs, each endpoint should adhere to strict enterprise security policies.
Ransomware attacks in particular can be dangerous, so it is important to keep remote access ports locked. Alternatively, you can configure firewalls to allow access only from known IP addresses.
Submitting biometric information or entering passcodes received via a verified email address or authenticator app are common ways to ensure only authorized users can access corporate resources.
In doing so, the VPN minimizes the risk of third parties intercepting data. However, it is essential to keep VPN software up-to-date to avoid any gaps in security.
However, these tools may see private IP addresses as an anomaly after you have enabled secure remote access. Therefore, you should make any adjustments needed to your SIEM software solution to allow employees to log in remotely while maintaining traceability.
Providing regular security and compliance training (and refresher courses) helps build awareness and understanding among your users, keeping the corporate network secure for the long term.
Many software updates close security gaps or improve existing security mechanisms to protect your organization from the latest threats. What’s more, you should always be running the latest antivirus and VPN software versions so you can take advantage of any new features.
TeamViewer Remote offers secure, efficient, and easy-to-use features designed to quickly fix issues and increase user or client satisfaction. Get in touch with our experts today or download the free version now.
In the past, IT security was the responsibility of the network team. They were expected to take care of remote access tools such as VPNs and firewalls.
But as working practices evolve, business priorities shift and the threat of cyberattacks increases, specialized cybersecurity teams are increasingly taking on these responsibilities. They ensure that the safety and security of business-critical data and systems is a top priority. Importantly, cybersecurity teams implement the technologies, policies, processes, and audits needed to identify, assess and mitigate remote access risks. This includes encrypting devices, implementing security standards, and cyber hygiene.
Your company can increase internal and external security with TeamViewer because we prioritize privacy and the protection of sensitive data. Our focus is not only on IT security but also on high compatibility and fast, stable remote connections. As a proven VPN alternative, you can start using TeamViewer immediately — setup is quick and easy, with no tedious configuration.
TeamViewer integrates with key business applications, providing comprehensive network security.